This blog is written only for EDUCATIONAL PURPOSE whatever you do isn't my responsibility its yours I only give Information here. Do everything at your own risk :)
Tuesday, 29 October 2013
Sunday, 27 October 2013
Huge Collection of E-Books
Huge Collection of Hacking E-Books.(Download Link provided Under the list)
(Ebook - Computer) Hacking The Windows Registry.pdf
(eBook - PDF) Hugo Cornwall - The Hacker's Handbook .pdf
(eBook pdf) Hacking into computer systems - a beginners guide.pdf
(ebook_-_pdf)_Hacking_IIS_Servers.pdf
0321108957.Addison-Wesley Professional.Honeypots- Tracking Hackers.pdf
0764578014.Wiley.The Database Hacker's Handbook- Defending Database Servers.chm
076459611X.John Wiley &_ Sons.Hacking GMail (ExtremeTech).pdf
1246523-Hacking.Guide.V3.1.pdf
1931769508.A-List Publishing.Hacker Linux Uncovered.chm
2212948-Hacker'S.Delight.chm
285063-Hacker.Bibel.pdf
3077366-HackerHighSchool.pdf
731986-Hacker's Desk Reference.pdf
A Beginners Guide To Hacking Computer Systems.pdf
Addison Wesley - Hackers Delight 2002.pdf
addison wesley - web hacking - attacks and defense.chm
Addison Wesley, The Outlook Answer Book Useful Tips Tricks And Hacks (2005) Bbl Lotb.chm
amazon-hacks.chm
Anti-Hacker ToolKit - McGraw Hill 2E 2004.chm
Attacking the DNS Protocol.pdf
Auerbach.Practical.Hacking.Techniques.and.Countermeasures.Nov.2006.pdf
Auerbach.Pub.The.Hackers.Handbook.The.Strategy.Behind.Breaking.into.and.Defending.Networks.Nov.20.pdf
bsd-hacks.pdf
ceh-official-certified-ethical-hacker-review-guide-exam-312-50.9780782144376.27422.pdf
Certified Ethical Hacker (CEH) v3.0 Official Course.pdf
Computer - Hackers Secrets - e-book.pdf
cracking-sql-passwords.pdf
Crc Press - The Hacker'S Handbook.pdf
Credit.Card.Visa.Hack.Ucam.Cl.Tr.560.pdf
DangerousGoogle-SearchingForSecrets.pdf
database hacker handbook.chm
Dummies - Hack How To Create Keygens (1).pdf
ebay-hacks-100-industrial-strength-tips-and-tools.pdf
ebook.oreilly.-.windows.xp.hacks.sharereactor.chm
eBooks.OReilly.-.Wireless.Hacks.100.Industrial.-.Strength.Tips.and.Tools.chm
ethical hacking, student guide.pdf
excel-hacks.chm
For.Dummies.Hacking.for.Dummies.Apr.2004.eBook-DDU.pdf
For.Dummies.Hacking.Wireless.Networks.For.Dummies.Sep.2005.eBook-DDU.pdf
google-hacks.pdf
Hack IT Security Through Penetration Testing.pdf
Hack Proofing - Your Network - Internet Tradecraft.pdf
Hack Proofing Linux A Guide to Open Source Security - Stangler, Lane - Syngress - ISBN 1-928994-34-2.pdf
Hack Proofing Sun Solaris 8.pdf
Hack Proofing Your E-Commerce Site.pdf
Hack Proofing Your Identity In The Information Age.pdf
Hack Proofing Your Network Second Edition.pdf
Hack Proofing Your Network_First Edition.pdf
Hack Proofing Your Web Applications.pdf
Hacker Disassembling Uncovered.chm
hacker ethic.pdf
Hacker Linux Uncovered.chm
Hacker Web Exploitation Uncovered.chm
Hacker'S.Delight.chm
hacker-disassembling-uncovered.9781931769228.20035.chm
Hackers Beware.pdf
Hackers Secrets Revealed.pdf
Hackers Secrets.pdf
Hackers, Heroes Of The Computer Revolution.pdf
Hackers_Secrets.pdf
Hacker_s_Guide.pdf
Hacking - Firewalls And Networks How To Hack Into Remote Computers.pdf
Hacking - The Art of Exploitation.chm
Hacking Cisco Routers.pdf
Hacking Exposed - Network Security Secrets & Solutions, 2nd Edition.pdf
Hacking Exposed Network Security Secrets & Solutions, Third Edition ch1.pdf
Hacking For Dummies 1.pdf
Hacking For Dummies 2.pdf
Hacking For Dummies.pdf
Hacking GMail.pdf
Hacking IIS Servers.pdf
Hacking into computer systems - a beginners guide.pdf
Hacking the Code - ASP.NET Web Application Security Cookbook (2004) .chm
hacking the windows registry .pdf
Hacking Windows XP.pdf
Hacking-ebook - CIA-Book-of-Dirty-Tricks1.pdf
Hacking-Hacker's Guide.pdf
Hacking-Hackers Secrets Revealed.pdf
Hacking-Hugo Cornwall-The Hacker's Handbook .pdf
Hacking-The Hacker Crackdown.pdf
Hacking.For.Dummies.Access.To.Other.People's.System.Made.Simple.pdf
Hacking.Guide.V3.1.pdf
Hackproofing Oracle Application Server.pdf
hacks.sfv
Hack_Attacks_Revealed_A_Complete_Reference_With_Custom_Security_Hacking_Toolkit.chm
Hack_IT_Security_Through_Penetration_Testing.chm
Halting.The.Hacker.A.Practical.Guide.To.Computer.Security.chm
How to Crack CD Protections.pdf
John Wiley & Sons - Hacking For Dummies.pdf
John.Wiley.and.Sons.Hacking.Windows.XP.Jul.2004.eBook-DDU.pdf
John.Wiley.and.Sons.Hacking.Windows.XP.Jul.2004.eBook.pdf
John.Wiley.and.Sons.The.Art.of.Intrusion.The.Real.Stories.Behind.the.Exploits.of.Hackers.Intruders. and.Deceivers.Feb.2005.ISBN0764569597.pdf
Jon.Erickson.Hacking.The.Art.Of.Exploitation.No.Starch.Press.2003.chm
linux-server-hacks.pdf
Linux-Server.Hacks-OReilly.pdf
little_black_book_oc_computer_viruses.pdf
mac-os-hacks.chm
McGraw Hill - Web Applications (Hacking Exposed).pdf
McGraw-Hill - Hacking Exposed, 3rd Ed - Hacking Exposed Win2.pdf
McGraw.Hacking.Exposed.Cisco.Networks.chm
McGraw.Hill.HackNotes.Linux.and.Unix.Security.Portable.Reference.eBook-DDU.pdf
McGraw.Hill.HackNotes.Network.Security.Portable.Reference.eB.pdf
McGraw.Hill.HackNotes.Network.Security.Portable.Reference.eBook-DDU.pdf
McGraw.Hill.HackNotes.Web.Security.Portable.Reference.eBook-.pdf
McGraw.Hill.HackNotes.Web.Security.Portable.Reference.eBook-DDU.pdf
McGraw.Hill.HackNotes.Windows.Security.Portable.Reference.eB.pdf
McGraw.Hill.HackNotes.Windows.Security.Portable.Reference.eBook-DDU.pdf
Mind Hacks - Tips & Tricks for Using Your Brain.chm
network-security-hacks.chm
No.Starch.Press.Hacking.The.Art.Of.Exploitation.chm
O'Reilly - Online Investing Hacks.chm
O'Reilly.-.Network.Security.Hacks.chm
O'Reilly.Windows.Server.Hack.chm
O'Reilly.Windows.Server.Hack.rar
online-investing-hacks.chm
OReilly Google Hacks, 1st Edition2003.pdf
OReilly - Flickr Hacks Tips and Tools for Sharing Photos Online (Feb 2006).chm
OReilly - Google Hacks.pdf
Oreilly Access Hacks Apr 2005.chm
Oreilly, Paypal Hacks (2004) Ddu.chm
OReilly,.Digital.Video.Hacks.(2005).DDU.LotB.chm
OReilly,.IRC.Hacks.(2004).DDU.chm
oreilly,.visual.studio.hacks.(2005).ddu.lotb.chm
Oreilly.Amazon.Hacks.eBook.LiB.chm
oreilly.firefox.hacks.ebook-lib.chm
OReilly.Google.Hacks.2nd.Edition.Dec.2004.ISBN0596008570.chm
OReilly.Google.Maps.Hacks.Jan.2006.chm
Oreilly.Linux.Desktop.Hacks.Mar.2005.eBook-LiB.chm
OReilly.Linux.Server.Hacks.Volume.Two.Dec.2005.chm
OReilly.Network.Security.Hacks.chm
OReilly.PayPal.Hacks.Sep.2004.eBook-DDU.chm
OReilly.PC.Hacks.Oct.2004.eBook-DDU.chm
OReilly.Perl.Hacks.Tips.and.Tools.for.Programming.Debugging.and.Surviving.May.2006.chm
OReilly.Skype.Hacks.Tips.and.Tools.for.Cheap.Fun.Innovative.Phone.Service.Dec.2005.chm
OReilly.SQL.Hacks.Nov.2006.chm
OReilly.Statistics.Hacks.May.2006.chm
OReilly.Ubuntu.Hacks.Tips.and.Tools.for.Exploring.Using.and.Tuning.Linux.Jun.2006.chm
OReilly.VoIP.Hacks.Tips.and.Tools.for.Internet.Telephony.Dec.2005.chm
oreilly.windows.xp.hacks.2nd.edition.feb.2005.lib.chm
OReilly.Word.Hacks.Oct.2004.eBook-DDU.chm
OSB.Ethical.Hacking.and.Countermeasures.EC.Council.Exam.312.50.Student.Courseware.eBook-LiB.chm
O_Reilly_-_Windows_XP_Hacks.chm
PC Games - How to Crack CD Protection.pdf
prentice hall - pipkin - halting the hacker- a practical guide to computer security, 2nd edition.chm
Que - UNIX Hints Hacks.chm
Que.Certified.Ethical.Hacker.Exam.Prep.Apr.2006.chm
Security and Hacking - Anti-Hacker Tool Kit Second Edition.chm
SoTayHacker1.0.chm
spidering-hacks.chm
SQL Hacks.chm
SQLInjectionWhitePaper.pdf
Syngress - Hack Proofing Linux (2001).pdf
Syngress - Hack Proofing Your Identity in the Information Age - 2002.pdf
Syngress - Hacking a Terror Network. The Silent Threat of Covert Channels.pdf
Syngress -- Hack Proofing Your Wireless Network.pdf
Syngress Hack Proofing Your Identity in the Information Age.pdf
Syngress.Buffer.Overflow.Attacks.Dec.2004.eBook-DDU.pdf
Syngress.Hack.the.Stack.Oct.2006.pdf
Syngress.Hacking.a.Terror.Network.Nov.2004.ISBN1928994989.pdf
The Little Black Book Of Computer Virus.pdf
the-database-hackers-handbook-defending-database-servers.9780764578014.25524.chm
The_20Little_20Black_20Book_20of_20Computer_20Viruses.pdf
tivo-hacks.100-industrial-strength-tips-and-tools.pdf
u23_Wiley - Hacking GPS - 2005 - (By Laxxuss).pdf
Websters.New.World.Websters.New.World.Hacker.Dictionary.Sep.2006.pdf
Wiley.Hacking.Firefox.More.Than.150.Hacks.Mods.and.Customizations.Jul.2005.eBook-DDU.pdf
Wiley.Hacking.Google.Maps.and.Google.Earth.Jul.2006.pdf
Wiley.Hacking.GPS.Mar.2005.ISBN0764598805.pdf
Wiley.Lifehacker.Dec.2006.pdf
Wiley.The.Database.Hackers.Handbook.Defending.Database.Servers.chm
Win XP Hacks oreilly 2003.chm
Windows Server Hacks.chm
WinXP SP1 Hack.pdf
Xbox-hack - AIM-2002-008.pdf
Yahoo.Hacks.Oct.2005.chm
Hackers Beware Defending Your Network From The Wiley Hacker.pdf
Download Links
-Admin
Its a huge collection so it has been divided into 11 parts please download all of them and you will get the books :)
Part 2
Part 3
Part 4
Part 5
Part 6
Part 7
Part 8
Part 9
Part 10
Part 11
-Admin
Visit My Website For More Ethical HackerMonday, 21 October 2013
5 Best Pen-Test Linux Distributions
5 Best Pen-Test Linux Distributions
Linux distributions are often customized to perform many specialized tasks cater to a particular industry, hobby or business. Security Penetration testing is one such niche where professional (and hobbyists) use customized Linux distributions with the whole purpose of doing security tests on networks and personal computer (hopefully with permission). Most of these distribution are live CDs which can be used without having to install them to your computer. Today we will take a look at some of best Pen-test distributions out there.
1) BackTrack:(Now Known as Kali) Kali/ Backtrack is the most widely known pen-test distribution out there. The latest release (4 Beta) has been ported to Debian/Ubuntu from Slackware and now can be installed locally as a full distribution and tools can be updated using Backtrack repositories. Backtrack includes more than 300+ security tools.
2) Knoppix STD: As the name suggests this distribution is based on Knoppix and STD stands forSecurity Tools Distribution. This distribution didn’t get any update (like most pen-test distros) in a long time and might not work on some new hardwares but they have a fairly good collection of tools.
xfcefluxbox is used for desktop environment.
3) nUbuntu: Based on Ubuntu and fluxbox, nUbuntu is a fairly new and active pen-test distribution. They have partnered with an Italian IT security company for future nUbuntu certification and training.
4) Network Security Toolkit: NST is a Fedora based Live distribution and unlike some other pen-test distro NST can be used under virtual machine without any network configuration problems (from my experience). NST also have a unique Web User Interface to access tools and manage configurations.
5) PEENTO: A Gentoo based pen-test live cd (you could have guessed) that actually looks very nice. They are using Enlightenment for DE and has quite a few unique pen-test tools including GPU based cracking software pyrit.
There used to be a time when there were a lot of active pen-test projects out there, but eventually most of them died off from lack of updates. Notably Auditor, WHAX ( later merged in to backtrack), PHLAK to name a few. Which pen-test live cd do you use or tried before?
Sunday, 20 October 2013
Hackers Mind Book
Are you new to the World of Hacking?Do you feel dumb when you don't know the meaning of a certain term? Well, then this will certainly help you out! This Dictionary Is Provided By Kevin Boss . If you are ever unsure about anything, simply scroll down and find that specific word, then read the definition.
Anything includes: Abbreviations, Phrases, Words, and Techniques.*The list is in alphabetical order for convenience!*
Abbreviations
★ DDoS = Distributed Denial of Service
★ DrDoS = Distributed Reflected Denial of Service Attack, uses a list of reflection servers or other methods such as DNS to spoof an attack to look like it's coming from multiple ips. Amplification of power in the attack COULD occur.
★ FTP =File Transfer Protocol. Used for transferring files over an FTP server.
★ FUD = Fully Undetectable
★ Hex =In computer science, hexadecimal refers to base-16 numbers. These are numbers that use digits in the range: 0123456789ABCDEF. In the C programming language (as well as Java, JavaScript, C++, and other places), hexadecimal numbers are prefixed by a 0x. In this manner, one can tell that the number 0x80 is equivalent to 128 decimal, not 80 decimal.
★ HTTP =Hyper Text Transfer Protocol. The foundation of data communication for the World Wide Web.
★ IRC = Internet Relay Chat. Transmiting text messages in real time between online users.
★ JDB =Java drive-by, a very commonly used web-based exploit which allows an attacker to download and execute malicious code locally on a slave's machine through a widely known java vulnerability.
★ Malware =Malicious Software
★ Nix = Unix based operating system, usually refered to here when refering to DoS'ing.
★ POP3 =This is the most popular protocol for picking up e-mail from a server.
★ R.A.T = Remote Administration Tool
★ SDB = Silent drive-by, using a zero day web-based exploit to hiddenly and un-detectably download and execute malicious code on a slave's system. (similar to a JDB however no notification or warning is given to the user)
★ SE = Social Engineering
★ Skid =Script Kid/Script Kiddie
★ SMTP =A TCP/IP protocol used in sending and receiving e-mail.
★ SQL =Structured Query Language. It's a programming language, that used to communicate with databases and DBMS. Can go along with a word after it, such as "SQL Injection."
★ SSH =Secure Shell, used to connect to Virtual Private Servers.
★ TCP = Transmission Control Protocol, creates connections and exchanges packets of data.
★ UDP =User Datagram Protocol, An alternative data transport to TCP used for DNS, Voice over IP, and file sharing.
★ VPN =Virtual Private Network
★ VPS =Virtual Private Server
★ XSS (CSS) = Cross Site Scripting
Words
★Algorithm = A series of steps specifying which actions to take in which order.
★ANSI Bomb = ANSI.SYS key-remapping commands consist of cryptic-looking text that specifies, using ansi numeric codes to redefine keys.
★Back Door = Something a hacker leaves behind on a system in order to be able to get back in at a later time.
★Binary = A numbering system in which there are only two possible values for each digit: 0 and 1.
★Black Hat = A hacker who performs illegal actions to do with hacking online. (Bad guy, per se)
★Blue Hat =A blue hat hacker is someone outside computer security consulting firms who is used to bug test a system prior to its launch, looking for exploits so they can be closed. Microsoft also uses the term BlueHat to represent a series of security briefing events.
★Bot = A piece of malware that connects computer to an attacker commonly using the HTTP or IRC protocal to await malicous instructions.
★Botnet = Computers infected by worms or Trojans and taken over by hackers and brought into networks to send spam, more viruses, or launch denial of service attacks.
★Buffer Overflow = A classic exploit that sends more data than a programmer expects to receive. Buffer overflows are one of the most common programming errors, and the ones most likely to slip through quality assurance testing.
★Cracker = A specific type of hacker who decrypts passwords or breaks software copy protection schemes.
★DDoS = Distributed denial of service. Flooding someones connection with packets. Servers or web-hosted shells can send packets to a connection on a website usually from a booter.
★Deface =A website deface is an attack on a site that changes the appearance of the site or a certain webpage on the site.
★Dictionary Attack = A dictionary attack is an attack in which a cyber criminal can attempt to gain your account password. The attack uses a dictionary file, a simple list of possible passwords, and a program which fills them in. The program just fills in every single possible password on the list, untill it has found the correct one. Dictionary files usually contain the most common used passwords.
★DOX = Personal information about someone on the Internet usualy contains real name, address, phone number, SSN, credit card number, etc.
★E-Whore = A person who manipulates other people to believe that he/she is a beautiful girl doing cam shows or selling sexual pictures to make money.
★Encryption = In cryptography, encryption applies mathematical operations to data in order to render it incomprehensible. The only way to read the data is apply the reverse mathematical operations. In technical speak, encryption is applies mathematical algorithms with a key that converts plaintext to ciphertext. Only someone in possession of the key can decrypt the message.
★Exploit = A way of breaking into a system. An exploit takes advantage of a weakness in a system in order to hack it.
★FUD = Fully undetectable, can be used in many terms. Generally in combination with crypters, or when trying to infect someone.
★Grey Hat = A grey hat hacker is a combination of a Black Hat and a White Hat Hacker. A Grey Hat Hacker may surf the internet and hack into a computer system for the sole purpose of notifying the administrator that their system has been hacked, for example. Then they may offer to repair their system for a small fee.Hacker (definition is widely disputed among people...) = A hacker is someone who is able to manipulate the inner workings of computers, information, and technology to work in his/her favor.
★Hacktivist = A hacktivist is a hacker who utilizes technology to announce a social, ideological, religious, or political message. In general, most hacktivism involves website defacement or denial-of-service attacks.
★IP Address = On the Internet, your IP address is the unique number that others use to send you traffic.
★IP Grabber = A link that grabs someone's IP when they visit it.
★Keylogger = A software program that records all keystrokes on a computer's keyboard, used as a surveillance tool or covertly as spyware.Leach = A cultural term in the warez community referring to people who download lots of stuff but never give back to the community.
★LOIC/HOIC = Tool(s) used by many anonymous members to conduct DDoS attacks. It is not recommended to use these under any circumstances.
★Malware =Software designed to do all kinds of evil stuff like stealing identity information, running DDoS attacks, or soliciting money from the slave.
Neophyte = A neophyte, "n00b", or "newbie" is someone who is new to hacking or phreaking and has almost no knowledge or experience of the workings of technology, and hacking.
★smith = Somebody new to a forum/game.
★OldFag = Somebody who's been around a forum/game for a long time.
★Packet = Data that is sent across the Internet is broken up into packets, sent individually across the network, and reassembled back into the original data at the other end.
★Phreak =Phone Freaks. Hackers who hack cell phones for free calling. Free Long distance calling. Etc.
★Phreaking = The art and science of cracking the phone network.
★Proxy = A proxy is something that acts as a server, but when given requests from clients, acts itself as a client to the real servers.
★Rainbow Table = A rainbow table is a table of possible passwords and their hashes. It is way faster to crack a password using rainbow tables then using a dictionary attack (Bruteforce).
★Remote Administration Tool =A tool which is used to remotely control (an)other machine(s). These can be used for monitoring user actions, but often misused by cyber criminals as malware, to get their hands on valuable information, such as log in credentials.
★Resolver =Software created to get an IP address through IM (instant messenger, like Skype/MSN) programs.
★Reverse Engineering = A technique whereby the hacker attempts to discover secrets about a program. Often used by crackers, and in direct modifications to a process/application.
★Root = Highest permission level on a computer, able to modify anything on the system without restriction.
★Rootkit (ring3 ring0) =A powerful exploit used by malware to conceal all traces that it exists. Ring3 - Can be removed easily without booting in safemode. Ring0 - Very hard to remove and very rare in the wild, these can require you to format, it's very hard to remove certain ring0 rootkits without safemode.
★Script Kiddie = A script kid, or skid is a term used to describe those who use scripts created by others to hack computer systems and websites. Used as an insult, meaning that they know nothing about hacking.
★Shell = The common meaning here is a hacked web server with a DoS script uploaded to conduct DDoS attacks via a booter. OR A shell is an script-executing unit - Something you'd stick somewhere in order to execute commands of your choice.
★Social Engineer = Social engineering is a form of hacking that targets people's minds rather than their computers. A typical example is sending out snail mail marketing materials with the words "You may already have won" emblazoned across the outside of the letter. As you can see, social engineering is not unique to hackers; it's main practitioners are the marketing departments of corporations.
★Spoof = The word spoof generally means the act of forging your identity. More specifically, it refers to forging the sender's IP address (IP spoofing). (Spoofing an extension for a RAT to change it from .exe to .jpg, etc.)
★SQL Injection =An SQL injection is a method often used to hack SQL databases via a website, and gain admin control (sometimes) of the site. You can attack programs with SQLi too.
★Trojan = A Trojan is a type of malware that masquerades as a legitimate file or helpful program with the ultimate purpose of granting a hacker unauthorized access to a computer.
★VPS = The term is used for emphasizing that the virtual machine, although running in software on the same physical computer as other customers' virtual machines, is in many respects functionallyequivalent to a separate physical computer, is dedicated to the individual customer's needs, has the privacy of a separate physical computer, and can be configured to run server software.
★Warez = Software piracy
★White Hat = A "white hat" refers to an ethical hacker, or a computer security expert, who specializes in penetration testing and in other testing methods to ensure the security of a businesses information systems. (Good guy, per se)
★Worm = Software designed to spread malware with little to no human interaction.
Zero Day Exploit = An attack that exploits a previously unknown vulnerability in a computer application, meaning that the attack occurs on "day zero" of awareness of the vulnerability. This means that the developers have had zero days to address and patch the vulnerability.
Anything includes: Abbreviations, Phrases, Words, and Techniques.*The list is in alphabetical order for convenience!*
Abbreviations
★ DDoS = Distributed Denial of Service
★ DrDoS = Distributed Reflected Denial of Service Attack, uses a list of reflection servers or other methods such as DNS to spoof an attack to look like it's coming from multiple ips. Amplification of power in the attack COULD occur.
★ FTP =File Transfer Protocol. Used for transferring files over an FTP server.
★ FUD = Fully Undetectable
★ Hex =In computer science, hexadecimal refers to base-16 numbers. These are numbers that use digits in the range: 0123456789ABCDEF. In the C programming language (as well as Java, JavaScript, C++, and other places), hexadecimal numbers are prefixed by a 0x. In this manner, one can tell that the number 0x80 is equivalent to 128 decimal, not 80 decimal.
★ HTTP =Hyper Text Transfer Protocol. The foundation of data communication for the World Wide Web.
★ IRC = Internet Relay Chat. Transmiting text messages in real time between online users.
★ JDB =Java drive-by, a very commonly used web-based exploit which allows an attacker to download and execute malicious code locally on a slave's machine through a widely known java vulnerability.
★ Malware =Malicious Software
★ Nix = Unix based operating system, usually refered to here when refering to DoS'ing.
★ POP3 =This is the most popular protocol for picking up e-mail from a server.
★ R.A.T = Remote Administration Tool
★ SDB = Silent drive-by, using a zero day web-based exploit to hiddenly and un-detectably download and execute malicious code on a slave's system. (similar to a JDB however no notification or warning is given to the user)
★ SE = Social Engineering
★ Skid =Script Kid/Script Kiddie
★ SMTP =A TCP/IP protocol used in sending and receiving e-mail.
★ SQL =Structured Query Language. It's a programming language, that used to communicate with databases and DBMS. Can go along with a word after it, such as "SQL Injection."
★ SSH =Secure Shell, used to connect to Virtual Private Servers.
★ TCP = Transmission Control Protocol, creates connections and exchanges packets of data.
★ UDP =User Datagram Protocol, An alternative data transport to TCP used for DNS, Voice over IP, and file sharing.
★ VPN =Virtual Private Network
★ VPS =Virtual Private Server
★ XSS (CSS) = Cross Site Scripting
Words
★Algorithm = A series of steps specifying which actions to take in which order.
★ANSI Bomb = ANSI.SYS key-remapping commands consist of cryptic-looking text that specifies, using ansi numeric codes to redefine keys.
★Back Door = Something a hacker leaves behind on a system in order to be able to get back in at a later time.
★Binary = A numbering system in which there are only two possible values for each digit: 0 and 1.
★Black Hat = A hacker who performs illegal actions to do with hacking online. (Bad guy, per se)
★Blue Hat =A blue hat hacker is someone outside computer security consulting firms who is used to bug test a system prior to its launch, looking for exploits so they can be closed. Microsoft also uses the term BlueHat to represent a series of security briefing events.
★Bot = A piece of malware that connects computer to an attacker commonly using the HTTP or IRC protocal to await malicous instructions.
★Botnet = Computers infected by worms or Trojans and taken over by hackers and brought into networks to send spam, more viruses, or launch denial of service attacks.
★Buffer Overflow = A classic exploit that sends more data than a programmer expects to receive. Buffer overflows are one of the most common programming errors, and the ones most likely to slip through quality assurance testing.
★Cracker = A specific type of hacker who decrypts passwords or breaks software copy protection schemes.
★DDoS = Distributed denial of service. Flooding someones connection with packets. Servers or web-hosted shells can send packets to a connection on a website usually from a booter.
★Deface =A website deface is an attack on a site that changes the appearance of the site or a certain webpage on the site.
★Dictionary Attack = A dictionary attack is an attack in which a cyber criminal can attempt to gain your account password. The attack uses a dictionary file, a simple list of possible passwords, and a program which fills them in. The program just fills in every single possible password on the list, untill it has found the correct one. Dictionary files usually contain the most common used passwords.
★DOX = Personal information about someone on the Internet usualy contains real name, address, phone number, SSN, credit card number, etc.
★E-Whore = A person who manipulates other people to believe that he/she is a beautiful girl doing cam shows or selling sexual pictures to make money.
★Encryption = In cryptography, encryption applies mathematical operations to data in order to render it incomprehensible. The only way to read the data is apply the reverse mathematical operations. In technical speak, encryption is applies mathematical algorithms with a key that converts plaintext to ciphertext. Only someone in possession of the key can decrypt the message.
★Exploit = A way of breaking into a system. An exploit takes advantage of a weakness in a system in order to hack it.
★FUD = Fully undetectable, can be used in many terms. Generally in combination with crypters, or when trying to infect someone.
★Grey Hat = A grey hat hacker is a combination of a Black Hat and a White Hat Hacker. A Grey Hat Hacker may surf the internet and hack into a computer system for the sole purpose of notifying the administrator that their system has been hacked, for example. Then they may offer to repair their system for a small fee.Hacker (definition is widely disputed among people...) = A hacker is someone who is able to manipulate the inner workings of computers, information, and technology to work in his/her favor.
★Hacktivist = A hacktivist is a hacker who utilizes technology to announce a social, ideological, religious, or political message. In general, most hacktivism involves website defacement or denial-of-service attacks.
★IP Address = On the Internet, your IP address is the unique number that others use to send you traffic.
★IP Grabber = A link that grabs someone's IP when they visit it.
★Keylogger = A software program that records all keystrokes on a computer's keyboard, used as a surveillance tool or covertly as spyware.Leach = A cultural term in the warez community referring to people who download lots of stuff but never give back to the community.
★LOIC/HOIC = Tool(s) used by many anonymous members to conduct DDoS attacks. It is not recommended to use these under any circumstances.
★Malware =Software designed to do all kinds of evil stuff like stealing identity information, running DDoS attacks, or soliciting money from the slave.
Neophyte = A neophyte, "n00b", or "newbie" is someone who is new to hacking or phreaking and has almost no knowledge or experience of the workings of technology, and hacking.
★smith = Somebody new to a forum/game.
★OldFag = Somebody who's been around a forum/game for a long time.
★Packet = Data that is sent across the Internet is broken up into packets, sent individually across the network, and reassembled back into the original data at the other end.
★Phreak =Phone Freaks. Hackers who hack cell phones for free calling. Free Long distance calling. Etc.
★Phreaking = The art and science of cracking the phone network.
★Proxy = A proxy is something that acts as a server, but when given requests from clients, acts itself as a client to the real servers.
★Rainbow Table = A rainbow table is a table of possible passwords and their hashes. It is way faster to crack a password using rainbow tables then using a dictionary attack (Bruteforce).
★Remote Administration Tool =A tool which is used to remotely control (an)other machine(s). These can be used for monitoring user actions, but often misused by cyber criminals as malware, to get their hands on valuable information, such as log in credentials.
★Resolver =Software created to get an IP address through IM (instant messenger, like Skype/MSN) programs.
★Reverse Engineering = A technique whereby the hacker attempts to discover secrets about a program. Often used by crackers, and in direct modifications to a process/application.
★Root = Highest permission level on a computer, able to modify anything on the system without restriction.
★Rootkit (ring3 ring0) =A powerful exploit used by malware to conceal all traces that it exists. Ring3 - Can be removed easily without booting in safemode. Ring0 - Very hard to remove and very rare in the wild, these can require you to format, it's very hard to remove certain ring0 rootkits without safemode.
★Script Kiddie = A script kid, or skid is a term used to describe those who use scripts created by others to hack computer systems and websites. Used as an insult, meaning that they know nothing about hacking.
★Shell = The common meaning here is a hacked web server with a DoS script uploaded to conduct DDoS attacks via a booter. OR A shell is an script-executing unit - Something you'd stick somewhere in order to execute commands of your choice.
★Social Engineer = Social engineering is a form of hacking that targets people's minds rather than their computers. A typical example is sending out snail mail marketing materials with the words "You may already have won" emblazoned across the outside of the letter. As you can see, social engineering is not unique to hackers; it's main practitioners are the marketing departments of corporations.
★Spoof = The word spoof generally means the act of forging your identity. More specifically, it refers to forging the sender's IP address (IP spoofing). (Spoofing an extension for a RAT to change it from .exe to .jpg, etc.)
★SQL Injection =An SQL injection is a method often used to hack SQL databases via a website, and gain admin control (sometimes) of the site. You can attack programs with SQLi too.
★Trojan = A Trojan is a type of malware that masquerades as a legitimate file or helpful program with the ultimate purpose of granting a hacker unauthorized access to a computer.
★VPS = The term is used for emphasizing that the virtual machine, although running in software on the same physical computer as other customers' virtual machines, is in many respects functionallyequivalent to a separate physical computer, is dedicated to the individual customer's needs, has the privacy of a separate physical computer, and can be configured to run server software.
★Warez = Software piracy
★White Hat = A "white hat" refers to an ethical hacker, or a computer security expert, who specializes in penetration testing and in other testing methods to ensure the security of a businesses information systems. (Good guy, per se)
★Worm = Software designed to spread malware with little to no human interaction.
Zero Day Exploit = An attack that exploits a previously unknown vulnerability in a computer application, meaning that the attack occurs on "day zero" of awareness of the vulnerability. This means that the developers have had zero days to address and patch the vulnerability.
Facebook tricks
Few Facebook Tricks
If you surf Facebook on daily basis or occasionally, chances are you’re already familiar with regular stuffs like add/delete friends, update statuses, walls and profile, add and explore pages & applications, etc, but there’s more..
How To Place Facebook Chat On Firefox Sidebar?
If you are using Firefox, you can place the Facebook Chat at the sidebar.Facebook Chat is cool, at least it allows you to send instant messages to online Facebook contacts. However I’m not really a fan of the chat bar being at the bottom of the page, what if I’ve left Facebook but still wants to remain chatting with my Facebook contacts? If you are using Firefox, you can place the Facebook Chat at the sidebar.
Step 1
Look for Bookmarks on the top navigation. Select Organize Bookmarks…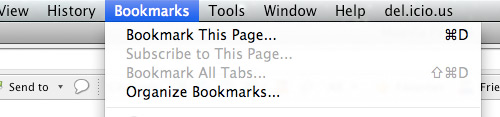
Step 2
Click New Bookmark... tab and enter the following:
- Name: Facebook Chat
- Location: http://www.facebook.com/presence/popout.php
- Check Load this bookmark in sidebar.
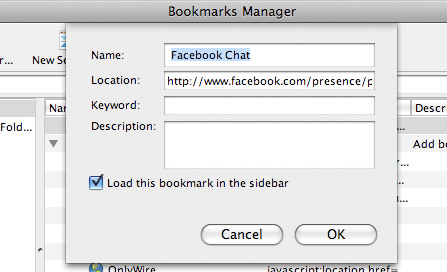
Step 3
Launch the Firefox sidebar, click Facebook Chat and start chatting with your Facebook contacts within Firefox.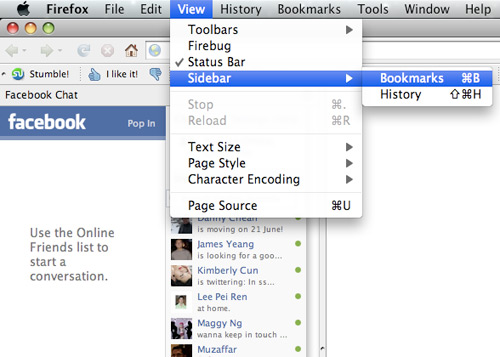
How To Download Facebook Photo Albums
FacePAD: Facebook Photo Album Downloader allows you to download your friends’ facebook albums, Events albums, and Group Albums, en masse, with the click of a button.How To Share Flickr Photos To Facebook
Flickr2Facebook is an unofficial Flickr to Facebook uploader(bookmarklet) which allows you upload photos to Facebook from Flickr.How To Update Facebook Without Using Facebook
hellotxt and Ping.fm both introduced features that let Facebook administrators update Facebook Pages.How To Schedule Facebook Messages
Sendible lets you schedule Facebook messages ahead of time so you can send messages to your friends, customers or colleagues in the future.How To "Friend" Someone On Facebook & Hide It From Your Status Updates?
A short tutorial on Makeuseof to guide you how to hide Facebook status updates and keep that fact confined to your closer friends.On your Facebook home page, you should see the ‘Settings’ menu close to the search field on your upper-right. Open that menu and go to ‘Privacy Settings’.
On the next page, you’ll have four choices: Profile, Search, News Feed, and Applications. What you’ll want to edit here are your Profile privacy settings.
By default, everything on your profile is limited to your Friends and your Networks (your first Network is likely your city of residence, but you may have joined more). From the screenshot above, you can see that I’ve limited everything on my profile to my Friends and their Friends. Anyone else who visits my profile will only see that I have a profile, but will not see what’s on it.
In my example, you’re going to want to edit the setting on your Status Updates, since you don’t want your boss to know that you’ve “fanned” the competition. Click that drop down menu and then select ‘Customize’.
You may want to tweak your overall privacy setting here, but what we’re aiming for is the “Except These People” list at the bottom of this dialog. Type out the name of any of your Friends to restrict that person from viewing anything in your Status Updates.
How To Create A Photo Collage Using Pictures Of Your Facebook Friends?
Here’s a small little trick in Facebook that allows you to create a grid view or photo collage out of your friends list. This is how I do it:
Click on Friends tab.Proceed to More tab.From "Choose an option" dropdown, choose any of the dashes "—"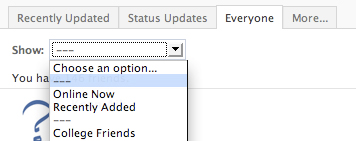
Photos of all your friends will be displayed, each in 50×50 pixels forming a grid view. Have fun.
1.How To Know When Facebook Friends Secretly Delete Or Block You
- This service has been discontinued. X-Friends is a unique tool for tracking friends that disappear from Facebook.
How To Display Selected Pictures Only On Your Facebook Profile Page
A little-known feature in Facebook that lets you decide who shows up in that Friends box. Click that "edit" pencil in your Friends box and type the names of your best friends in the box that says "Always show these friends"How To Remove Facebook Advertisements
This Greasemonkey script – Facebook: Cleaner removes many of the annoying ads and updates that unavoidably appear on your Facebook pages.How To Syncs Photos Of Facebook Friends With Contacts In Microsoft Outlook
OutSync is a free Windows application that syncs photos of your Facebook friends with matching contacts in Microsoft Outlook. It allows you to select which contacts are updated. So you can update all contacts at once or just a few at a time.How To Display Facebook Statuses On WordPress Blog?
The following method make use of Facebook status feed and WordPress RSS widget to display Facebook Statuses on WordPress blog.. It will also work for self-host WordPress blogs.Step 1Login into Facebook. Under Profile, look for Mini Feed column, click onSee All.
Step 2
Under Mini Feed, click on ‘Status Stories‘ on the right column. Scroll all the way to the bottom, look for ‘My Status‘
Step 3
Copy the link of My Status, and we are about to use this in WordPress blog. Your link will look something like the following:
Step 4 (WordPress)
Under WordPress admin, Navigate to Design -> Widget. Look for RSS Widget, add it to your side bar.
Step 5
Paste the copied URL inside, give it a name, save and your Facebook statuses (or status depends on how many you display) will now appear on your WordPress blog.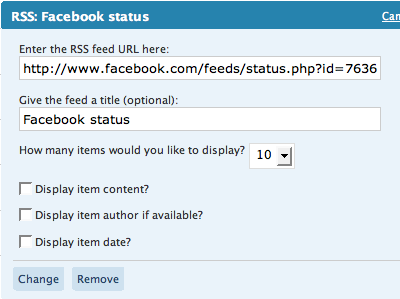
How To Post Your Blog Posts To Your Facebook Wall Automatically
Wordbook allows you to cross-post your blog posts to your Facebook Wall. Your Facebook “Boxes” tab will show your most recent blog posts.How To Access Facebook Chat On Desktop
Gabtastik and digsby let you keep Facebook chat sessions open on your Windows desktop outside of your regular web browser, using minimal screen real estate and system memory.How To Create Quiz On Facebook Easily
LOLapps provides quiz creator that can be employed to conjure up these popular personality quizzes that are so widespread in Facebook.How To Hide Your Online Status On Facebook Chat From Select Contacts
Facebook has integrated friends list with Chat and you can also choose which of these list members get to see you online.How To Get Facebook Updates On Email
NutshellMail consolidates your Facebook accounts through the inbox you use the most.How To Update Facebook Status From Firefox
FireStatus is a status update utility for multiple social networks, including FaceBook.How To Get Facebook On Your Desktop
Seesmic Desktop, Facebooker, Xobni, Facebook Sidebar Gadget, Scrapboy and Facebook AIR application are desktop applications that allows you interact with your stream just as you would on Facebook, but without the browser.
Crypters
 Crypters are computer applications which are solely used to bypass the antivirus detection of malwares. Hackers use crypters to hide viruses, Trojans, RATS, keyloggers and other hacktools into a new executable, whose sole purpose is to bypass the detection of the same from antivirus. Crypters are basically dead programs which does not affect the actual functionality of the program, they just spoof the actual program behind their encryption and make antivirus fool. Most antivirus detects viruses on basis of heuristics and normal string based detection. Since we have spoofed the original program, so antivirus stand lame and does not detect it as virus.
Crypters are computer applications which are solely used to bypass the antivirus detection of malwares. Hackers use crypters to hide viruses, Trojans, RATS, keyloggers and other hacktools into a new executable, whose sole purpose is to bypass the detection of the same from antivirus. Crypters are basically dead programs which does not affect the actual functionality of the program, they just spoof the actual program behind their encryption and make antivirus fool. Most antivirus detects viruses on basis of heuristics and normal string based detection. Since we have spoofed the original program, so antivirus stand lame and does not detect it as virus.
Common terms related to crypters:
For understanding and designing crypters, hackers must be aware of certain terms, most of you already know these terms, but as i am writing this tutorial starting from novice level and take it to elite level at the end. So if you knowthese terms just read them one more time, as that might help you to clear some of your doubts.
1. FUD or UD : Fully undetectable(FUD) means that your virus is not detected by any of the existing antiviruses while undetectable(UD) means detectable by few antiviruses. FUD is our only goal and elite hackers always rely on that.
Note: Crypter will remain FUD until you have openly shared on internet. Public crypters remains FUD up to maximum 2 to 3 days then they become UD. So if you want to use crypter for long time so never publish and share that on internet. Use it anonymously.
2. STUB : A stub is a small piece of code which contains certain basic functionality which is used again and again. It is similar to package in Java or simply like header files in C ( which already has certain standard functions defined in it). A stub basically simulates the functionality of existing codes similarly like procedures on remote machines or simply PC's. In crypters, client side server is validated using stubs, so never delete stub file from your crypter. Stubs adds portability to crypter code, so that it can be used on any machine without requiring much procedures and resources on other machines.
Let me explain with small example:
Suppose you are writing a code that converts bytes to bits, so we know formula or method for converting bytes to bits will remain same and it will be independent of machine. So our stub (or method stub or procedure) will contain something like this:
BEGIN
totalBits = calculateBits(inputBytes)
Compute totalBits = inputBytes * 8
END
Now what we will pass is only number of bytes to this stub. And it will return the resulting bits. Similarly, we include some common machine independent checks and functions in our stub, and in main code we only passes linkage and inputs to these stubs, which in return provides suitable results.
Note: Most of times it happens, suppose you downloaded some keylogger and you complain to provider its not working, only reason for that is stub. Also always kept in your mind, if you are downloading any keylogger or crypter always check stub is present in it. If not, don't download it, its just a piece of waste and for sure hacker is spreading his virus using that. I recommend that never download any hacking tool on your real machine, always use virtual machine or sandbox to test hack tools.
3. USV: Unique stub version or simply USV is a part of crypter that generates a unique version of stub which differentiates it from its previous stub, thus makes it more undetectable against antiviruses. For detecting this antivirus companies has to reverse engineer your crypter stub, that is not that easy to do, so it will remain undetectable for long time. This consist of one most important component USG ( unique stub generation) which is the actual part of crypter that encrypts and decrypts the original file means its the heart of your algorithm and i will recommend never write this part in stub, rather include this part in main code. Why i am saying this, stub is part of code which is shared with victim, so it will become public and hence your Crypter will not remain FUD for much long time.
Different types of crypters:
1. External Stub based crypters : This category consists of public crypters (those you have downloaded till date :P (noobish one's) and you complains to provider that its detectable by antiviruses. That really foolish complaint, if crypter is public then it can never remain FUD. So don't ever complain to me also after my next article for such noobish things. Ahahah.. i got deviated for real thing.
External Stub based crypters are those crypters in which most of the functionality of the crypter depends of external stub, if your delete that stub file, your crypter is useless. :P Most antivirus only do that. These type of crypters contains two files one is client.exe and other is stub.exe . Stub contains the main procedures and client contains the global functions that call those procedures.
2. Internal or Inbuilt stub based crypters: The crypters that contains only one exe file (i.e client) fall under this category. This client file has inbuilt stub in it. You can separate stub and client part here too using RCE (reverse code engineering) but it is not recommended.
Note: External or Internal stub doesn't make much difference as antivirus detects files on the basis of strings related to offsets. Whenever you reverse engineer any application or program, the program execution flow will gonna remain the same but offsets may change. USV will come into picture at this point. If you include your encryption algorithm separately then it will be more harder for antivirus to detect your crypter.
3. Run time crypters: Run time crypters are those crypters which remain undetected in memory during their execution. We are looking for these type of crypters only. :P These can any of the two above.
4. Scan time crypters: Those crypters which will remain undetected while encrypting the files but will become detectable when resultant file is generated. :P Fking one's that wastes all effort we have put. This really annoys everything is working fine and at last you get your file being detected by noob antiviruses.
Saturday, 19 October 2013
For All those Beginners (Important Must Read ) :)
Posted From Facebook Group (My Friends)
Some Tutorial Links
study, one day we will be the best :)
netcat:
link : http://adf.ly/XoVk0
Video : http://adf.ly/XoVtW
E-Books : http://adf.ly/XoW3F
wireshark:
E-Book : http://adf.ly/XoWBw
Link : http://adf.ly/XoWHd
Video : http://adf.ly/XoWOJ (Part 1)
Video : http://adf.ly/XoWT3 (Part 2)
Video : http://adf.ly/XoWWL (Part 3)
Psexec:
Video : http://adf.ly/XoWw9
Link : http://adf.ly/XoX1D
Nmap:
Video : http://adf.ly/XoX5H
Link : http://adf.ly/XoXOq
aircrack-ng:
Link : http://adf.ly/XoXUQ (many tutorials for aircrack-ng on this page )
oclHashcat:
Link : http://adf.ly/XoXh5
Metasploit:
Link : http://adf.ly/XoXuD (many tutorials for metasploit on this page )
Scapy:
Video : http://adf.ly/XoXyX
Links : http://adf.ly/XoY1x // http://adf.ly/XoY68
Reaver:
Link : http://adf.ly/XoYAY
John the Ripper:
Links : http://adf.ly/XoYEu // http://adf.ly/XoYJ0
Ettercap:
Links : http://adf.ly/XoYMX
http://adf.ly/XoYQq
http://adf.ly/XoYTQ
http://adf.ly/XoYVN
dsniff:
Links : http://adf.ly/XoYYR // http://adf.ly/XoYaq
Some Tutorial Links
study, one day we will be the best :)
netcat:
link : http://adf.ly/XoVk0
Video : http://adf.ly/XoVtW
E-Books : http://adf.ly/XoW3F
wireshark:
E-Book : http://adf.ly/XoWBw
Link : http://adf.ly/XoWHd
Video : http://adf.ly/XoWOJ (Part 1)
Video : http://adf.ly/XoWT3 (Part 2)
Video : http://adf.ly/XoWWL (Part 3)
Psexec:
Video : http://adf.ly/XoWw9
Link : http://adf.ly/XoX1D
Nmap:
Video : http://adf.ly/XoX5H
Link : http://adf.ly/XoXOq
aircrack-ng:
Link : http://adf.ly/XoXUQ (many tutorials for aircrack-ng on this page )
oclHashcat:
Link : http://adf.ly/XoXh5
Metasploit:
Link : http://adf.ly/XoXuD (many tutorials for metasploit on this page )
Scapy:
Video : http://adf.ly/XoXyX
Links : http://adf.ly/XoY1x // http://adf.ly/XoY68
Reaver:
Link : http://adf.ly/XoYAY
John the Ripper:
Links : http://adf.ly/XoYEu // http://adf.ly/XoYJ0
Ettercap:
Links : http://adf.ly/XoYMX
http://adf.ly/XoYQq
http://adf.ly/XoYTQ
http://adf.ly/XoYVN
dsniff:
Links : http://adf.ly/XoYYR // http://adf.ly/XoYaq
-Admin
Visit My Website For More WebsitePassword Crackers ;)
This post helps you to unlock rar,iso files password for free.....
2. John the Ripper :
3. THC Hydra :
4. Aircrack :
5. L0phtcrack :
6. Airsnort :
7. SolarWinds :
8. Pwdump :
9. RainbowCrack :
10. Brutus :
The best password crackers. The list made from all password brealkers from all over the globe including versions from unix and widnows as well.
1. Cain and Abel :
1. Cain and Abel :
The top password recovery tool for Windows
UNIX users often smugly assert that the best free security tools support their platform first, and Windows ports are often an afterthought. They are usually right, but Cain & Abel is a glaring exception. This Windows-only password recovery tool handles an enormous variety of tasks. It can recover passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
UNIX users often smugly assert that the best free security tools support their platform first, and Windows ports are often an afterthought. They are usually right, but Cain & Abel is a glaring exception. This Windows-only password recovery tool handles an enormous variety of tasks. It can recover passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
2. John the Ripper :
A powerful, flexible, and fast multi-platform password hash cracker
John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. It supports several crypt(3) password hash types which are most commonly found on various Unix flavors, as well as Kerberos AFS and Windows NT/2000/XP LM hashes
John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. It supports several crypt(3) password hash types which are most commonly found on various Unix flavors, as well as Kerberos AFS and Windows NT/2000/XP LM hashes
3. THC Hydra :
A Fast network authentication cracker which support many different services
When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more then 30 protocols, including telnet, ftp, http, https, smb, several databases, and much more
When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more then 30 protocols, including telnet, ftp, http, https, smb, several databases, and much more
4. Aircrack :
The fastest available WEP/WPA cracking tool
Aircrack is a suite of tools for 802.11a/b/g WEP and WPA cracking. It can recover a 40 through 512-bit WEP key once enough encrypted packets have been gathered. It can also attack WPA 1 or 2 networks using advanced cryptographic methods or by brute force. The suite includes airodump (an 802.11 packet capture program), aireplay (an 802.11 packet injection program), aircrack (static WEP and WPA-PSK cracking), and airdecap (decrypts WEP/WPA capture files)
Aircrack is a suite of tools for 802.11a/b/g WEP and WPA cracking. It can recover a 40 through 512-bit WEP key once enough encrypted packets have been gathered. It can also attack WPA 1 or 2 networks using advanced cryptographic methods or by brute force. The suite includes airodump (an 802.11 packet capture program), aireplay (an 802.11 packet injection program), aircrack (static WEP and WPA-PSK cracking), and airdecap (decrypts WEP/WPA capture files)
5. L0phtcrack :
Windows password auditing and recovery application
L0phtCrack, also known as LC5, attempts to crack Windows passwords from hashes which it can obtain (given proper access) from stand-alone Windows NT/2000 workstations, networked servers, primary domain controllers, or Active Directory. In some cases it can sniff the hashes off the wire. It also has numerous methods of generating password guesses (dictionary, brute force, etc). LC5 was discontinued by Symantec in 2006, but you can still find the LC5 installer floating around. The free trial only lasts 15 days, and Symantec won't sell you a key, so you'll either have to cease using it or find a key generator. Since it is no longer maintained, you are probably better off trying Cain and Abel, John the Ripper, or Ophcrack instead.
L0phtCrack, also known as LC5, attempts to crack Windows passwords from hashes which it can obtain (given proper access) from stand-alone Windows NT/2000 workstations, networked servers, primary domain controllers, or Active Directory. In some cases it can sniff the hashes off the wire. It also has numerous methods of generating password guesses (dictionary, brute force, etc). LC5 was discontinued by Symantec in 2006, but you can still find the LC5 installer floating around. The free trial only lasts 15 days, and Symantec won't sell you a key, so you'll either have to cease using it or find a key generator. Since it is no longer maintained, you are probably better off trying Cain and Abel, John the Ripper, or Ophcrack instead.
6. Airsnort :
802.11 WEP Encryption Cracking Tool
AirSnort is a wireless LAN (WLAN) tool that recovers encryption keys. It was developed by the Shmoo Group and operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered. You may also be interested in the similar Aircrack.
AirSnort is a wireless LAN (WLAN) tool that recovers encryption keys. It was developed by the Shmoo Group and operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered. You may also be interested in the similar Aircrack.
7. SolarWinds :
A plethora of network discovery/monitoring/attack tools
SolarWinds has created and sells dozens of special-purpose tools targeted at systems administrators. Security-related tools include many network discovery scanners, an SNMP brute-force cracker, router password decryption, a TCP connection reset program, one of the fastest and easiest router config download/upload applications available and more.
SolarWinds has created and sells dozens of special-purpose tools targeted at systems administrators. Security-related tools include many network discovery scanners, an SNMP brute-force cracker, router password decryption, a TCP connection reset program, one of the fastest and easiest router config download/upload applications available and more.
8. Pwdump :
A window password recovery tool
Pwdump is able to extract NTLM and LanMan hashes from a Windows target, regardless of whether Syskey is enabled. It is also capable of displaying password histories if they are available. It outputs the data in L0phtcrack-compatible form, and can write to an output file.
Pwdump is able to extract NTLM and LanMan hashes from a Windows target, regardless of whether Syskey is enabled. It is also capable of displaying password histories if they are available. It outputs the data in L0phtcrack-compatible form, and can write to an output file.
9. RainbowCrack :
An Innovative Password Hash Cracker
The RainbowCrack tool is a hash cracker that makes use of a large-scale time-memory trade-off. A traditional brute force cracker tries all possible plaintexts one by one, which can be time consuming for complex passwords. RainbowCrack uses a time-memory trade-off to do all the cracking-time computation in advance and store the results in so-called "rainbow tables". It does take a long time to precompute the tables but RainbowCrack can be hundreds of times faster than a brute force cracker once the precomputation is finished.
The RainbowCrack tool is a hash cracker that makes use of a large-scale time-memory trade-off. A traditional brute force cracker tries all possible plaintexts one by one, which can be time consuming for complex passwords. RainbowCrack uses a time-memory trade-off to do all the cracking-time computation in advance and store the results in so-called "rainbow tables". It does take a long time to precompute the tables but RainbowCrack can be hundreds of times faster than a brute force cracker once the precomputation is finished.
10. Brutus :
A network brute-force authentication cracker
This Windows-only cracker bangs against network services of remote systems trying to guess passwords by using a dictionary and permutations thereof. It supports HTTP, POP3, FTP, SMB, TELNET, IMAP, NTP, and more. No source code is available. UNIX users should take a look at THC Hydra.
This Windows-only cracker bangs against network services of remote systems trying to guess passwords by using a dictionary and permutations thereof. It supports HTTP, POP3, FTP, SMB, TELNET, IMAP, NTP, and more. No source code is available. UNIX users should take a look at THC Hydra.
Subscribe to:
Comments (Atom)




